
Why Container Versioning Matters
Versioning seems like a basic concept – just tagging an image – but in reality, it plays a crucial role in ensuring stability and traceability. But for me, versioning is important and something many people tend to overlook or not fully consider. I learned the importance of versioning the hard way when my team spent hours debugging a production issue, only to realize that an unintended image update was the root cause. Apparently, a DevOps engineer had set the tag to latest, which silently pulled a newer version, causing unexpected behavior. That experience showed me firsthand how critical proper container versioning is for ensuring stable deployments and avoiding surprises.
Managing container images effectively is a key part of a smooth CI/CD process. For organizations deploying container-native applications, choosing the right tools for building, running, and managing containers in production is essential. Image versioning, in particular, plays a major role in maintaining control and predictability across environments.
In the container ecosystem, versioning is commonly referred to as tagging, which differs from traditional software versioning in several key ways. One major difference is that container tags are not fixed – they can be reassigned to different image layers over time. Additionally, multiple tags can reference the same underlying set of layers, allowing for more flexible image management.
This approach is widely used across popular open-source container images. For example, in Docker Hub, the Nginx image tags illustrate how different versions can point to the same or evolving image layers. Below is a screenshot of the Nginx tag descriptions on Docker Hub.
Supported tags and respective Dockerfile links
1.27.4, mainline, 1, 1.27, latest, 1.27.4-bookworm, mainline-bookworm, 1-bookworm, 1.27-bookworm, bookworm
Each row in the list represents a distinct Nginx image, likely incorporating different extensions or application versions. For example, the row includes the tags 1.27.4, mainline, 1, 1.27, and latest-all of which currently reference the same image layers.
Assigning multiple tags to the same image is a common practice that helps consumers understand tag stability. Some tags, like latest, are frequently updated, while others, such as version-specific tags (1.27.4), remain unchanged to ensure consistency and reproducibility.
A common convention is to tag every release as latest, regardless of whether it is a development snapshot or a final release. Each successful CI/CD pipeline run updates the latest tag, causing it to point to new image layers. While this is convenient for development, it is not ideal for production deployments, where stability is a priority.
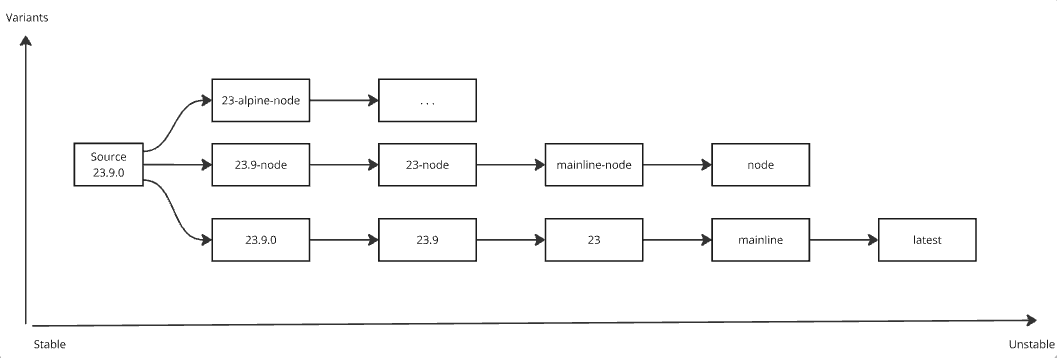
To give teams more control over image updates and their impact, tag names often convey context. For example, a tag like 23.9 typically represents the most recent patch release within that version series – such as 23.9.1, 23.9.2, and 23.9.3. This allows users to track minor updates while ensuring compatibility within a specific version range.
Importance of container versioning
Properly versioning container images is essential for DevOps teams to track changes between releases. Using explicit versioning is especially important when working with publicly available container images or dependencies on other containers.
Relying on an image tagged as latest for an upstream dependency poses a risk. Since the latest tag will eventually point to a different set of image layers, an engineer might unknowingly introduce breaking changes without modifying their Dockerfile. By specifying an exact version, they ensure consistency and avoid unexpected side effects.
Version numbers should also align with the release cycle, allowing teams to trace changes back to project milestones. This makes it easier to identify potential breaking changes and maintain a structured update process.
Another key benefit of proper versioning is the ability to quickly roll back to a previous state if needed. In some cases, multiple versions of the same application must remain active simultaneously. For instance, a company may need to support backward compatibility for web services used by clients. Versioning allows teams to orchestrate multiple image versions efficiently, ensuring smooth transitions and minimal disruptions.
Image tagging strategy
When adopting container technology, engineering teams need to define an image tagging strategy that aligns with their workflow. Establishing a clear tagging approach upfront ensures smoother integration with CI/CD pipelines, enabling consistent version control and easier management of container artifacts. With a standardized strategy in place, both developers and the operations team can quickly identify which version of an image is being used.
Available image tagging strategies
Image ID (Digest)
A digest (or image ID) is a cryptographic hash that uniquely identifies a container image based on its contents. Since digests ensure immutability, they are ideal for production environments where absolute certainty about an image’s contents is required. However, since they are not human-readable, they are best suited for automated systems rather than manual tracking.
Rolling Tags
Rolling tags (e.g., latest, stable) dynamically update to point to new images. This strategy is useful in development environments, where always pulling the latest version is beneficial. However, rolling tags are risky for production, as they may introduce unintended changes. If used in production, they should be combined with strict testing and monitoring.
Semantic Versioning (SemVer) Tags
SemVer tags follow a structured format (MAJOR.MINOR.PATCH), making it easy to understand the impact of changes:
- Major (
2.0.0) – Breaking changes - Minor (
2.1.0) – New features, backward-compatible - Patch (
2.1.1) – Bug fixes
This approach is ideal for both production and CI/CD workflows, as it ensures backward compatibility and automation-friendly versioning.
GitCommit Tags
Git commit-based tags link a container image directly to a specific code commit (e.g., a1b2c3d). This provides full traceability between the code and the built image, making it a good choice for debugging, rollback, and auditing changes. However, commit hashes are not user-friendly, so they are best combined with other strategies like SemVer.
Timestamp-Based Tags
Timestamps (e.g., 2025-03-11) indicate when an image was built. This is useful for tracking build history and troubleshooting issues but does not provide direct context about code changes. Timestamps are best used in development and testing environments rather than production.
Build ID Tags
Build IDs (e.g., build-1023) are generated by CI/CD pipelines and link an image to a specific build process. They are useful for troubleshooting and rollback in automated environments but should be paired with other strategies, such as GitCommit or SemVer, for clarity.
Looking back at my experience, that production issue was a tough lesson – but one that fundamentally changed how I approach container versioning. This shift has significantly reduced unexpected issues and made debugging far more manageable.
If there’s one takeaway from my journey, it’s this: container versioning isn’t just about tagging images – it’s about creating predictability, stability, and trust in your deployments. Whether you’re running a small project or managing large-scale infrastructure, having a well-thought-out versioning strategy can save you from countless hours of troubleshooting.