
Why PrivateLinks: Securing Cloud Communications the Right Way
During one of the projects I’ve worked on, I had to design a cloud environment that could meet Department of Defense (DoD) compliance standards. It wasn’t just about encryption, IAM, or a checklist of best practices. The real challenge was this: No service, no matter how basic, could expose a public endpoint.
This might sound simple on paper, but in practice, it fundamentally reshapes how you build and manage cloud architectures. You can’t just flip a switch and make everything private – you have to rethink everything from the ground up.
The client is connected to government contracts that require full adherence to DoD network isolation policies that have to include these requirements:
- No public IPs – even internal control plane traffic had to be isolated
- No fallback to public endpoints – even for metadata, DNS, or health checks
- DNS resolution must point to private IPs only
At first, I thought: This is overkill. But the more I dug in, the more I saw how subtle leaks can happen through cloud defaults. You’d be surprised how many services automatically try to phone home to public endpoints for updates, health checks, or telemetry. All of that had to be locked down.
The Solution: PrivateLink Everything
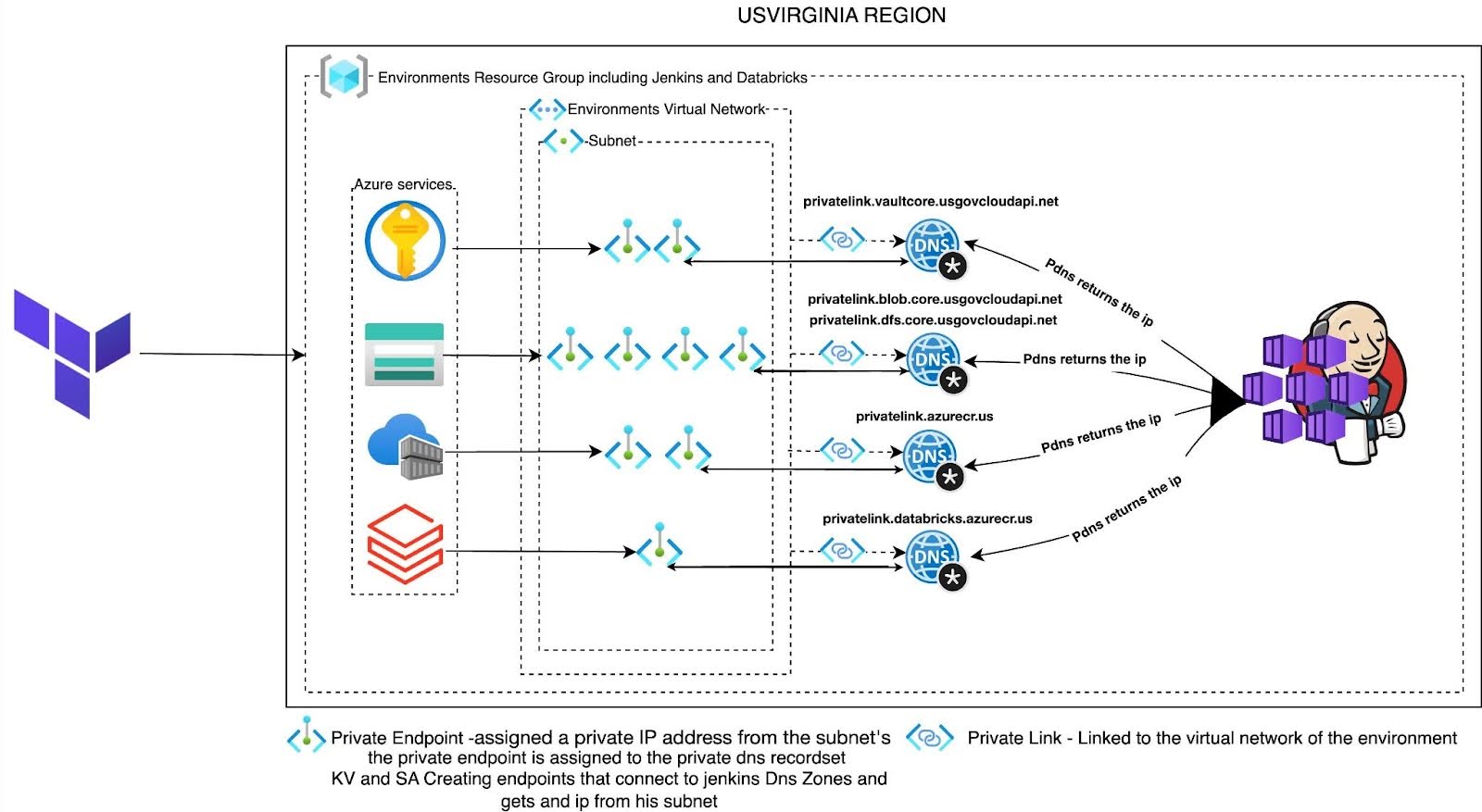
After I understood the level of isolation that was required to achieve this task, I thought about something that might be a little bit drastic: every cloud service we create must have a PrivateLink attached. If the service doesn’t support PrivateLinks, we’ll wrap it behind one. No exceptions.
That understanding of the full architecture and requirements led me to a lot of architectural changes that took months to implement properly:
I had to refactor most of the Terraform modules to automatically provision the private endpoints when different services are created. This wasn’t just copy-paste work – each service had its own quirks and connection patterns that needed custom handling.
I built private DNS zones for every supported service and resolved a bunch of DNS override headaches that came with it. Getting DNS right in a fully private environment is trickier than you’d think because you’re essentially creating your own version of the internet inside your VPC.
The networking topology became way more complex. We needed multiple layers of routing, custom NAT configurations, and careful subnet planning to make sure everything could still talk to each other without ever touching the public internet.
The Reality: Everything Changes
After we implemented those changes, most of the architecture of the environment was transformed, and the team had to change their approach in how they handle different tasks during their day. Simple things like launching new tools in the environment or providing support for different teams (developers, QA) became more involved because now every bit of traffic that travels in the cloud should stay in it without going out to the public internet.
The weird thing is, once we got it working, it actually made some things easier. The refactor helped us give less support about connection issues between different apps and environments in the cloud because everything was predictable and contained. No more mysterious timeouts or intermittent connectivity problems caused by public internet routing.
But it wasn’t all smooth sailing. There were plenty of moments where I was troubleshooting why some service couldn’t reach another, only to realize it was trying to use a public endpoint that we’d blocked. Those debugging sessions taught me more about cloud networking than years of regular projects.
Beyond Technical: The Human Element
This project pushed me outside my comfort zone in ways I didn’t expect. I had to learn about compliance frameworks, private DNS strategies, and deal with non-technical stakeholders who cared more about the impact than the technical details. Explaining why we needed to spend weeks on “invisible” infrastructure changes to people who just wanted their applications to work was its own challenge.
The Mindset Shift
It also shifted how I think about “security by default.” Now, I believe that in any enterprise environment, especially ones touching government or finance, you should start from a zero-public-access mindset. It makes your environment more secure, faster, and more trusted, but it also forces you to be intentional about every connection and dependency in your system.
The project taught me that true security isn’t about adding layers on top of existing architecture – it’s about designing the foundation to be secure from day one. It’s harder upfront, but it pays off in the long run with fewer surprises and more predictable behavior.
Working on DoD-compliant infrastructure taught me that extreme requirements often lead to better solutions. When you’re forced to question every default setting and every automatic connection, you end up with a more deliberate, robust architecture. Yes, it’s more complex initially, but that complexity is intentional and controlled rather than accidental.
If you’re working in highly regulated industries, don’t wait for compliance requirements to force your hand. Start thinking about zero-trust networking from day one. Your future self – and your security team – will thank you for it.
The next time someone tells you a security requirement is “overkill,” take a step back and ask: what if this becomes the baseline? Because in my experience, today’s extreme requirements have a way of becoming tomorrow’s industry standards.